Subscribe to:
Post Comments (Atom)
Popular Posts
-
Application profiling Addresses the unique structure, logic, and features of an individual, highly customized web application. Applic...
-
NIDS – Network Intrusion Detection System • It Uses a network tap, span port, or hub to collect packets on the network • Attempts t...
-
USING METASPLOIT windows/local/s4u_persistence windows/local/vss_persistence windows/local/registry_persistence windows/manage...
-
Importance Of Policies To Reduce Risks Organization implement policies to reduce risks without policies their are no rules and that ...
-
Installing pupy git clone https://github.com/n1nj4sec/pupy.git pupy cd pupy git submodule init git submodule update pip install -r pu...
-
Footprinting (Also Known As Reconnaissance) Is The Technique Used For Gathering Information About Computer Systems And The Entit...
-
Target Specification 192. 168. 100. 1-50 IP Range 192. 168. 100. 1/24 CIDR Spec. -iL Filename IP Addr File -iR...
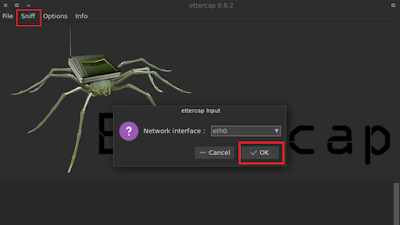


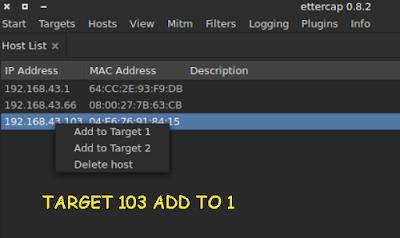




















No comments:
Post a Comment