A firewall is a network security system, either hardware- or software-based, that uses rules to control incoming and outgoing network traffic.
Firewall Software which protects individual PC users from malware and hacking attacks, can be downloaded from trusted security companies and are easily accessible by the public.
Types Of Firewall
- Hardware Firewall
- Software Firewall
Hardware Firewall
A hardware firewall uses a PC-like appliance to run software that blocks unwanted outside traffic. A firewall appliance may allow the firewall administrator to simply drag and drop various rules into place. For example, if your business wishes to block all incoming traffic from particular top level domains (TLD’s), such as particular country codes, a few clicks will give the option of blocking incoming, outgoing or both types of traffic to/from those TLD’s. Likewise, if a given user group – perhaps your tech support operation – needs to run Microsoft Remote Desktop Connection (RDC) to assist users on another network, that entire group can be dragged and dropped into an “authorized users” category while the RDC application can be dropped into an “authorized application” category.
Updating a firewall appliance with new rules to prevent evolving threats, hacks and malware is straightforward: a single update protects all machines connected on the network. Further, many firewall appliances are delivered with additional security features that may include VPN services, intrusion detection and others that would normally have to be purchased and configured separately.
Software Firewall
These software products know what application is attempting to make a connection with the Internet or other network as well as the protocols that should be used. If the firewall software detects an attempted connection that is not contained in its rules database, it can be configured to prompt the user to accept or reject the connection. Malicious traffic, whether it is outgoing as in the case of malware on a user’s PC attempting to send data outside the network – or incoming – can be blocked.
Hardware Vs Software Firewall
Then, activate the client-side software firewalls that come with Microsoft, Apple and Linux operating systems to protect each PC client. The client-side firewall running on each machine provides packet filtering and monitors the state of traffic generated by various end user applications.
Types Of Software Firewall
- Network-Level Firewall
- Circuit-Level Firewall
- Application-Level Firewall
- Stateful Multi-level Firewall
Network-Level Firewall
Inspects packet headers and filters traffic based on the IP address and port of the source and the destination. Some applications could also filter packets based on protocols, the domain name and a few other attributes.
Network-level firewalls are fast, built into most network appliances, particularly routers.
don't support sophisticated rule-based models. They don't understand languages like HTML and XML,
Capable of decoding SSL-encrypted packets to examine their content. but can't validate user inputs or detect maliciously modified parameters in an URL request. This leaves your network vulnerable to a number of serious threats.
Possible Attacks :
- IP Address Spoofing
- Source Routing
- Fragmentation
Circuit-Level Firewall
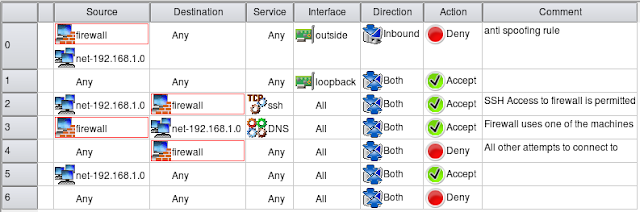
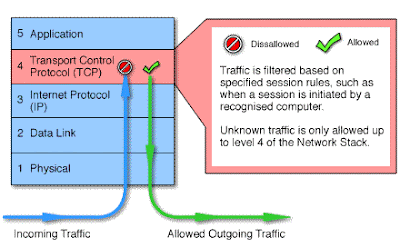
These are second-generation of firewall technology, it can monitor TCP handshaking between packets to make sure a session is legitimate. Traffic is filtered based on specified session rules and may be restricted to recognized computers only. Circuit-level firewalls hide the network itself from the outside, which is useful for denying access to intruders. But they don't filter individual packets.
Application-Level Firewall
Also called proxy firewalls, looks more deeply into the application data going through their filters. By considering the context of client requests and application responses, these firewalls attempt to enforce correct application behavior, block malicious activity and help organizations ensure the safety of sensitive information and systems. They can log user activity too. Application-level filtering may include protection against spam and viruses as well, and be able to block undesirable Web sites based on content rather than just their IP address.
The downside to deep packet inspection is that the more closely a firewall examines network data flow, the longer it takes, and the heavier hit your network performance will sustain. This is why the highest-end security appliances include lots of RAM to speed packet processing. And of course it increases the cost.
Stateful Multi-level Firewall
Filters packets at the network level and recognizes and process application-level data, but since they don't employ proxies, they deliver reasonably good performance in spite of the deep packet analysis. On the downside, they are not cheap, and they can be difficult to configure and administer.
Dual-Homed Firewall
A dual-homed host is a term used to reference a type of firewall that uses two (or more) network interfaces. One connection is an internal network and the second connection is to the Internet. A dual-homed host works as a simple firewall provided there is no direct IP traffic between the Internet and the internal network.
Multi-Homed Firewall
A multi-homed host is a host (a firewall in this case) that has more than one network interface, with each interface connected to logically and physically separate network segments. A dual-homed host (host with two interfaces) is the most common instance of a multi-homed host.
Next-Generation Firewall
A Next-Generation Firewall (NGFW) is a part of the third generation of firewall technology, combining a traditional firewall with other network device filtering functionalities, such as an application firewall using in-line deep packet inspection (DPI), an intrusion prevention system (IPS). Other techniques might also be employed, such as TLS/SSL encrypted traffic inspection, website filtering, QoS/bandwidth management, antivirus inspection and third-party identity management integration (i.e. LDAP, RADIUS, Active Directory)
Web Application Firewall
A web application firewall (WAF) is an application firewall for HTTP applications. It applies a set of rules to an HTTP conversation. Generally, these rules cover common attacks such as cross-site scripting (XSS) and SQL injection.
While proxies generally protect clients, WAFs protect servers. A WAF is deployed to protect a specific web application or set of web applications. A WAF can be considered a reverse proxy.
WAFs may come in the form of an appliance, server plugin, or filter, and may be customized to an application. The effort to perform this customization can be significant and needs to be maintained as the application is modified.


















No comments:
Post a Comment