Subscribe to:
Post Comments (Atom)
Popular Posts
-
Application profiling Addresses the unique structure, logic, and features of an individual, highly customized web application. Applic...
-
NIDS – Network Intrusion Detection System • It Uses a network tap, span port, or hub to collect packets on the network • Attempts t...
-
Download Boson binder Download image upload to icoconvert and convert into ico 256*256 Now you have binder, image, ico & payload Bo...
-
Importance Of Policies To Reduce Risks Organization implement policies to reduce risks without policies their are no rules and that ...
-
USING METASPLOIT windows/local/s4u_persistence windows/local/vss_persistence windows/local/registry_persistence windows/manage...
-
WINDOWS 8.1 PRIVILEGE ESCALATION BY BYPASSING UAC PHYSICALLY This tool works as you can see in the picture in win 8.1, but it's li...
-
Confidentiality The first goal of Network Security is "Confidentiality". The function of "Confidentiality" is in...

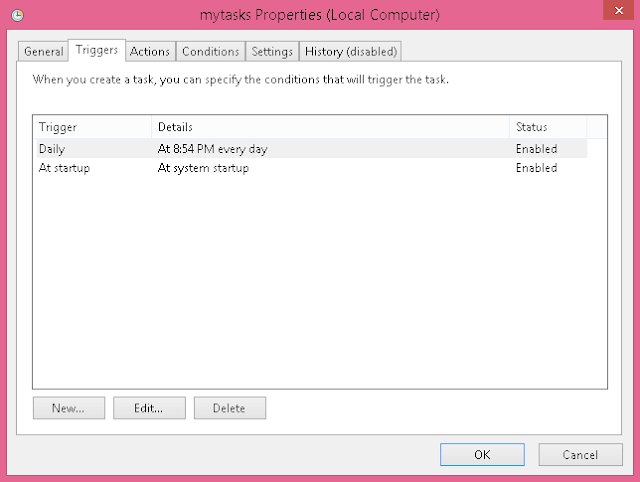

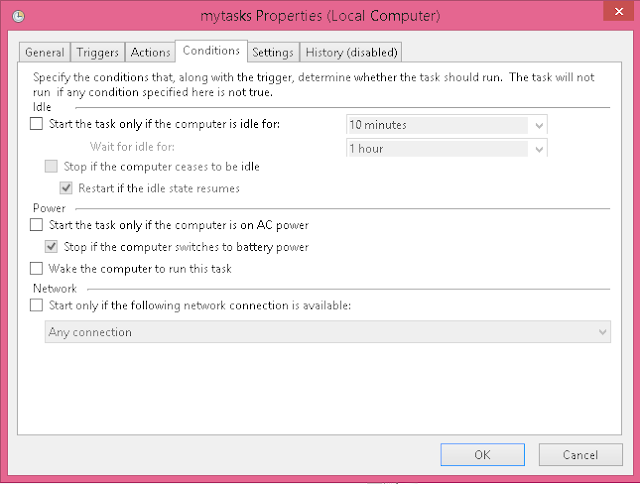












No comments:
Post a Comment